Hash vs Encryption vs Encoding
Hash
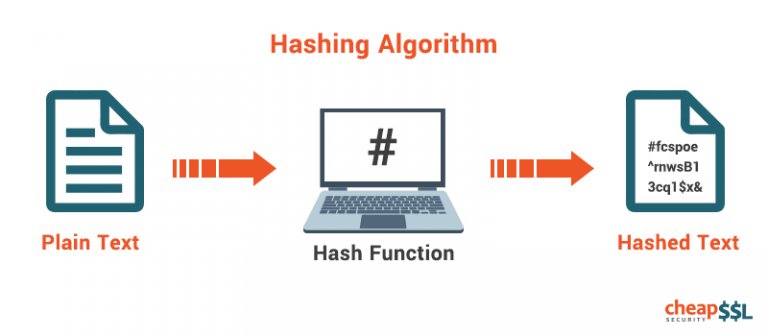
Note: above diagram comes from cheapsslsecurity
It has following properties:
- Generally, hash is smaller than its original data
- Hash value is fixed length for one type hash algorithm
- Same data will always produce same Hash
- Impossible to revert hash value back to original data
- No collision, different text corresponds to different hash
- Unpredictability, if we change even a single character in the input (actually even a single bit), on average 50% of the output bits will change
Common Usage
- check content integrity
- store user password
Encryption
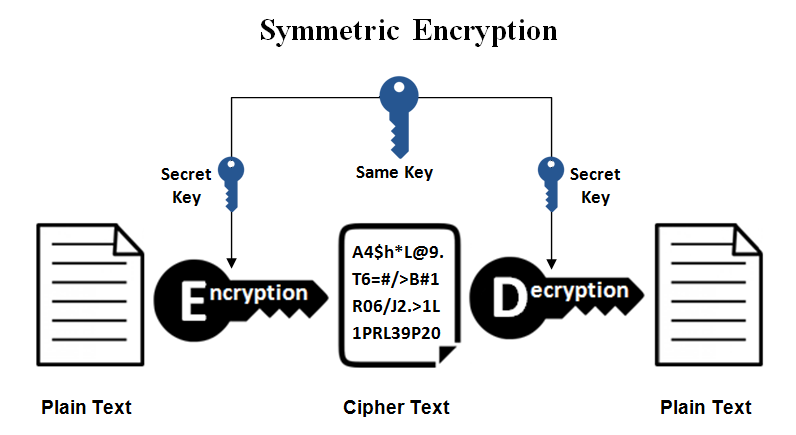
Symmetric
It uses same key to encrypt and decrypt.
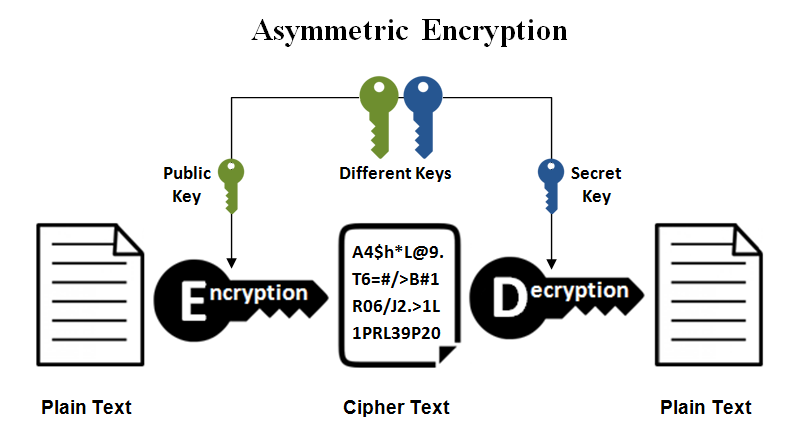
Asymmetric
It uses public key to encrypt and private key to decrypt.
The public key, as its name implies, is public which means it can be passed over the internet.
Hybrid
Combine symmetric with asymmetric.
Hash vs Encryption
| Hash | Symmetric | Asymmetric | |
|---|---|---|---|
| no. of keys | 0 | 1 | 2 |
| recommended length | 256 bits | 128 bits | 2048 bits |
| commonly used algorithm | SHA | AES | RSA |
| key distirbution | N/A | big issue pass the key over internet |
easy & secure |
| speed | fast | fast | relatively slow |
| complexity | medium | medium | high |
Encoding
Encoding is not used for security purpose.
Fundamentally, it is just a technique to transform data into other formats so that it can be consumed by others.
The same algorithm, such as ASCII, is used to encode and decode.
Reference
Written on April 17, 2019