SSL(TLS)
Terms
| term | remark |
|---|---|
| SSL | Secure Sockets Layer |
| TLS | Transport Layer Security |
| HTTPS | Hypertext Transfer Protocol Secure |
| HSTS | HTTP Strict Transport Security |
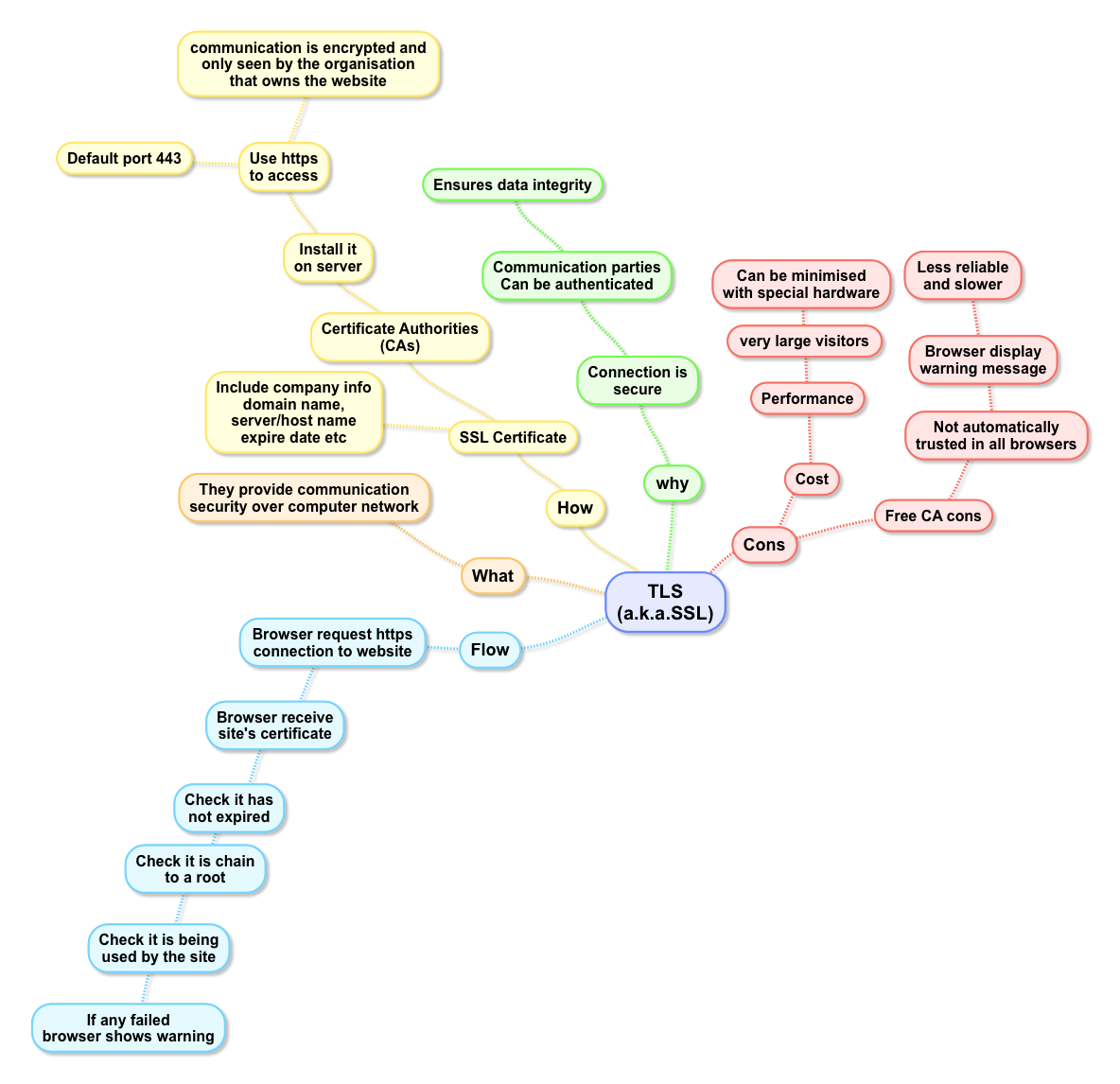
In HTTPS, the communication protocol is encrypted using TLS(SSL).
It is recommended to use HTTP Strict Transport Security (HSTS) with HTTPS to protect users from man-in-the-middle attacks, especially SSL stripping.
SSL/TLS encryption can be configured in two modes - simple and mutual:
- In simple mode, authentication is only performed by the server.
- The mutual version requires the user to install a personal client certificate in the web browser for user authentication
Note: HTTPS only secure the process of transmitting data over internet
What is CA
CA(certificate authority) is an entity which issues digital certificates to organizations or people after validating them. CA have to keep detailed records of what has been issued and the information used to issue it, and are audited regularly to make sure that they are following defined procedures.
Root Certificate
The certificate that you purchase to secure your web site must be digitally signed by another certificate that is already in the trusted store of your user’s web browser.
By doing this, the web browser will automatically trust your certificate because it is issued by someone that it already trusts.
If it isn’t signed by a trusted root certificate, or if links in the certificate chain are missing, then the web browser will give a warning message that the web site may not be trusted.
So browser compatibility means that the certificate you buy is signed by a root certificate that is already trusted by most web browsers that your customers may be using.
Single domain/sub-domain
Most SSL server certificates will only secure a single domain name or sub-domain. For example, a certificate could secure www.yourdomain.com or mail.yourdomain.com but not both.
The certificate will still work on a different domain name but the web browser will give an error anytime it sees that the address in the address bar doesn’t match the domain name (called a common name) in the certificate.
Multiple domains/sub-domains
If you need to secure multiple sub-domains on a single domain name, you can buy a wildcard certificate. For a wildcard certificate, a common name of *.yourdomain.com would secure www.yourdomain.com, mail.yourdomain.com, secure.yourdomain.com, etc… There are also special certificates such as Unified Communications (UC) certificates that can secure several different domain names in one certificate.
SSL keys
Essentially, three keys are used to set up the SSL connection:
- public key
- private key
- session key
Anything encrypted with the public key can only be decrypted with the private key, and vice versa.
Because encrypting and decrypting with private and public key takes a lot of processing power, they are only used during the SSL Handshake to create a symmetric session key. After the secure connection is made, the session key is used to encrypt all transmitted data.
Flow
- Browser connects to a web server (website) secured with SSL (https). Browser requests that the server identify itself.
- Server sends a copy of its SSL Certificate, including the server’s public key.
- Browser checks the certificate root against a list of trusted CAs and that the certificate is unexpired, unrevoked, and that its common name is valid for the website that it is connecting to. If the browser trusts the certificate, it creates, encrypts, and sends back a symmetric session key using the server’s public key.
- Server decrypts the symmetric session key using its private key and sends back an acknowledgement encrypted with the session key to start the encrypted session.
- Server and Browser now encrypt all transmitted data with the session key.